centos7_firewall_high_traffic_ntp
Table of Contents
CentOS 7 - high traffic NTP and netfilter
The default firewalld ntp service uses connection tracking. Something you don't want when managing high traffic. This page describes how to disable connection tracking.
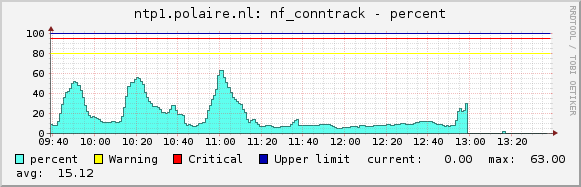
NF connection tracking list in percentage, before and after.
- Default firewalld NTP service rule:
-A IN_public_allow -p udp -m udp --dport 123 -m conntrack --ctstate NEW -j ACCEPT
- Show conntrack count:
# sysctl -a | egrep "conntrack_max|conntrack_count" net.netfilter.nf_conntrack_count = 13362 net.netfilter.nf_conntrack_max = 65536
Configure legacy iptables scripts
In the following steps I will disable firewalld and use the legacy iptables scripts.
- Install iptables-services:
yum install iptables-services
- Configure iptables, edit /etc/sysconfig/iptables, check if sshd is allowed…
# Generated by iptables-save v1.4.21 on Tue Aug 25 15:27:32 2015 *mangle :PREROUTING ACCEPT [19:1444] :INPUT ACCEPT [19:1444] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [19:1444] :POSTROUTING ACCEPT [19:1444] COMMIT # Completed on Tue Aug 25 15:27:32 2015 # Generated by iptables-save v1.4.21 on Tue Aug 25 15:27:32 2015 *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [1:76] -A INPUT -m conntrack --ctstate INVALID -j DROP -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p udp -m udp --dport 123 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited COMMIT # Completed on Tue Aug 25 15:27:32 2015 # Generated by iptables-save v1.4.21 on Tue Aug 25 15:27:32 2015 *raw :PREROUTING ACCEPT [12:912] :OUTPUT ACCEPT [11:836] -A PREROUTING -p udp -m udp --dport 123 -j CT --notrack -A OUTPUT -p udp -m udp --sport 123 -j CT --notrack COMMIT # Completed on Tue Aug 25 15:27:32 2015 # Generated by iptables-save v1.4.21 on Tue Aug 25 15:27:32 2015 *nat :PREROUTING ACCEPT [5:380] :INPUT ACCEPT [5:380] :OUTPUT ACCEPT [1:76] :POSTROUTING ACCEPT [1:76] COMMIT # Completed on Tue Aug 25 15:27:32 2015
- Stop and disable firewalld:
systemctl disable firewalld systemctl stop firewalld systemctl status firewalld
- Start iptables service:
systemctl enable iptables systemctl start iptables
- Check conntrack count:
# sysctl -a | egrep "conntrack_max|conntrack_count" net.netfilter.nf_conntrack_count = 2 net.netfilter.nf_conntrack_max = 65536
Disable connection tracking in RouterOS (Mikrotik)
- Add fasttrack action before accepting connection.
centos7_firewall_high_traffic_ntp.txt · Last modified: 2021/10/09 15:14 by 127.0.0.1
