raspberry_pi_openlabs_6lowpan
Table of Contents
Raspberry Pi - 802.15.4 radio
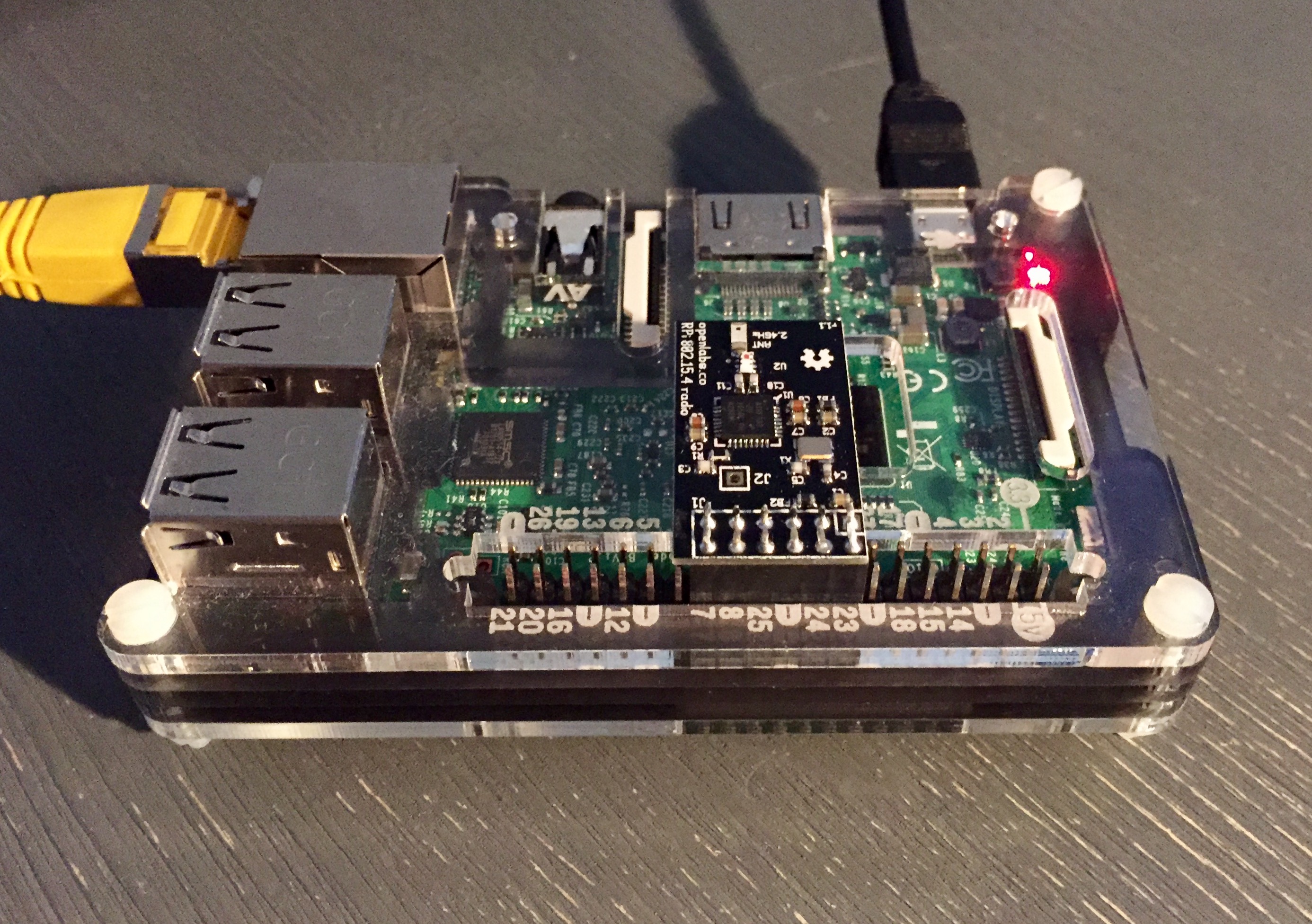
This guide helps you to run the the openlabs 802.15.4 radio connected to spi0.0, pin 15-26. For this guide I used a Raspberry Pi 3, raspbian with kernel 4.9.34-v7+ and an openlabs 802.15.4 (at86rf233) radio.
- Documentation, mailinglist http://wpan.cakelab.org/
Preparation
- Connect the openlabs 802.15.4 radio to pin 15-26, see image above.
- Install and configure the latest version of raspbian.
- Edit
/boot/config.txt, add the following:dtoverlay=at86rf233 dtparam=spi=on
- Reboot.
- If everything went well, the device should be recognized:
$ dmesg |grep spi [ 3.504882] at86rf230 spi0.0: Detected at86rf233 chip version 1 $ ip link show wpan0 3: wpan0: <BROADCAST,NOARP> mtu 123 qdisc noop state DOWN mode DEFAULT group default qlen 300 link/ieee802.15.4 1e:59:ad:54:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff:ff:ff - If you don't use the internal WiFi/Bluetooth, you can rfkill the chip:
apt-get install rfkill rfkill 0 rfkill 1
- Or completely disable the chip, add to
/boot/config.txt:dtoverlay=pi3-disable-wifi dtoverlay=pi3-disable-bt
Compile and install wpan-tools
- Install required libnl library and wireshark:
sudo apt-get install libnl-3-dev libnl-genl-3-dev wireshark
- Download latest tools from http://wpan.cakelab.org/
- Compile the wpan tools:
tar xf http://wpan.cakelab.org/releases/wpan-tools-0.7.tar.xz cd wpan-tools-0.7/ ./configure make sudo make install
WPAN ping
Ping at IEEE 802.15.4 level.
- Set-up server:
ip link set wpan0 down iwpan phy0 set channel 0 15 iwpan dev wpan0 set pan_id 0x1111 iwpan dev wpan0 set short_addr 0x0001 ip link set wpan0 up wpan-ping -d 0x0002 # Listen for sort address 0x0002
- Then ping from client:
ip link set wpan0 down iwpan phy0 set channel 0 15 iwpan dev wpan0 set pan_id 0x1111 iwpan dev wpan0 set short_addr 0x0002 ip link set wpan0 up $ wpan-ping -a 0x0001 -s 5 -c5 PING 0x0001 (PAN ID 0x1111) 5 data bytes 5 bytes from 0x0001 seq=0 time=4.9 ms 5 bytes from 0x0001 seq=1 time=4.8 ms 5 bytes from 0x0001 seq=2 time=5.1 ms 5 bytes from 0x0001 seq=3 time=5.8 ms 5 bytes from 0x0001 seq=4 time=4.7 ms --- 0x0001 ping statistics --- 5 packets transmitted, 5 received, 0% packet loss rtt min/avg/max = 4.695/5.075/5.818 ms
6loWPAN, IPv6 over 802.15.4
- Node 1:
ip link set lowpan0 down ip link set wpan0 down iwpan dev wpan0 set pan_id 0xcafe iwpan phy0 set channel 0 26 ip link add link wpan0 name lowpan0 type lowpan ip link set wpan0 up ip link set lowpan0 up ip addr add 2001:db8::1/64 dev lowpan0
- Node 2:
ip link set lowpan0 down ip link set wpan0 down iwpan dev wpan0 set pan_id 0xcafe iwpan phy0 set channel 0 26 ip link add link wpan0 name lowpan0 type lowpan ip link set wpan0 up ip link set lowpan0 up ip addr add 2001:db8::2/64 dev lowpan0
- Ping over IPv6:
ping6 2001:db8::1 PING 2001:db8::1(2001:db8::1) 56 data bytes 64 bytes from 2001:db8::1: icmp_seq=1 ttl=64 time=26.4 ms 64 bytes from 2001:db8::1: icmp_seq=2 ttl=64 time=14.6 ms 64 bytes from 2001:db8::1: icmp_seq=3 ttl=64 time=13.5 ms 64 bytes from 2001:db8::1: icmp_seq=4 ttl=64 time=14.5 ms ^C --- 2001:db8::1 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3004ms rtt min/avg/max/mdev = 13.577/17.334/26.477/5.297 ms
Monitor mode, packet capture
- Configure monitor mode (as root):
ip link set monitor0 down ip link set lowpan0 down ip link set wpan0 down iwpan dev monitor0 del iwpan dev lowpan0 del iwpan dev wpan0 set pan_id 0x1111 iwpan phy0 set channel 0 15 iwpan phy phy0 interface add monitor0 type monitor ip link set monitor0 up
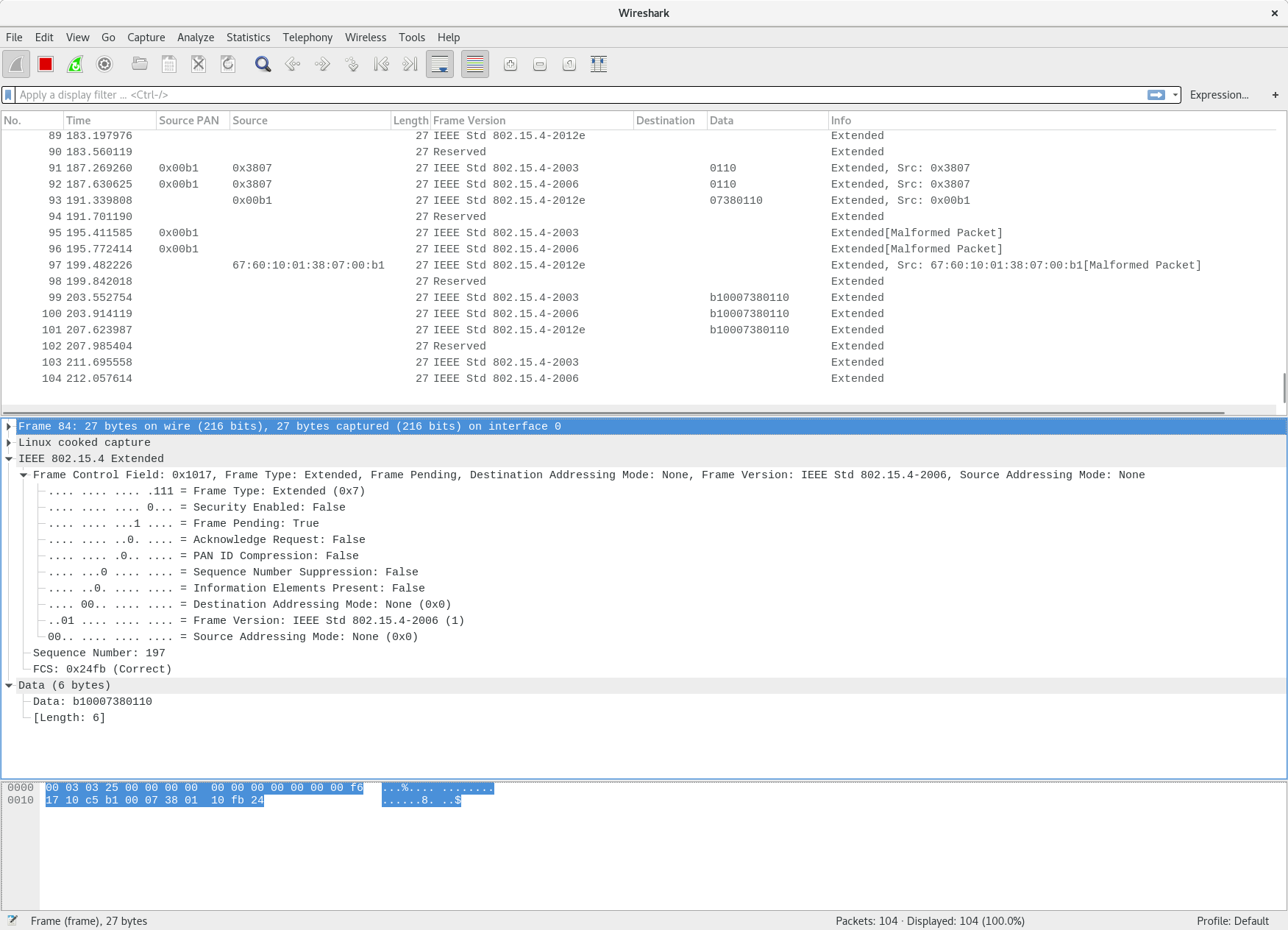
- Capture packets with wireshark, or tshark:
$ tshark -i monitor0 Capturing on 'monitor0' 1 0.000000 -> IEEE 802.15.4 26 Reserved 2 1.015518 -> IEEE 802.15.4 26 Reserved 3 2.031011 -> IEEE 802.15.4 26 Reserved 4 2.447961 -> IEEE 802.15.4 27 Reserved 5 2.808887 -> IEEE 802.15.4 27 Reserved 6 3.046981 -> IEEE 802.15.4 26 Reserved 7 5.080265 0x0100 -> IEEE 802.15.4 26 Reserved, Src: 0x0100, Bad FCS 8 6.091876 0x0100 -> IEEE 802.15.4 26 Reserved, Src: 0x0100 9 6.518924 0x3807 -> IEEE 802.15.4 27 Reserved, Src: 0x3807 10 6.880309 0x3807 -> IEEE 802.15.4 27 Reserved, Src: 0x3807 11 9.141103 -> IEEE 802.15.4 26 Reserved[Malformed Packet] 12 10.156867 -> IEEE 802.15.4 26 Reserved[Malformed Packet] 13 10.589015 0x3807 -> IEEE 802.15.4 27 Reserved, Src: 0x3807 14 10.949083 0x3807 -> IEEE 802.15.4 27 Reserved, Src: 0x3807 15 11.169899 -> IEEE 802.15.4 26 Reserved[Malformed Packet] 16 12.186160 -> IEEE 802.15.4 26 Reserved[Malformed Packet] 17 14.219155 -> IEEE 802.15.4 26 Reserved, Bad FCS 18 14.657224 -> IEEE 802.15.4 27 Reserved[Malformed Packet] 19 15.018708 -> IEEE 802.15.4 27 Reserved[Malformed Packet] 20 15.235625 -> IEEE 802.15.4 26 Reserved, Bad FCS ^C20 packets captured
- Examples:
# Filter packets from specific source tshark -i monitor0 -V -Y "wpan.src16==0x0100" # Filter packets from specific source PAN tshark -i monitor0 -V -Y "wpan.src_pan==0xfcff" # CSV example tshark -i monitor0 -Y "wpan.src_pan==0x00b1" -Tfields -E separator=, -E quote=d -e wpan.src_pan -e wpan.src16 -e data
raspberry_pi_openlabs_6lowpan.txt · Last modified: 2021/10/09 15:14 by 127.0.0.1