strongswan_ipsec_os_x
strongSwan & OS X 10.8.x
Install software
- Install Debian 7
- apt-get install build-essential
- apt-get ntp gmp libgmp3-dev
- download strongswan-5.0.4.tar.gz
- ./configure
- make
- make install
Configure server
iptables
#Allow ipsec iptables -A INPUT -p udp -i eth0 -d $EXT0 --dport 500 -m state --state NEW,ESTABLISHED -j ACCEPT iptables -A INPUT -p udp -i eth0 -d $EXT0 --dport 4500 -m state --state NEW,ESTABLISHED -j ACCEPT iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -m policy --dir out --pol ipsec -j ACCEPT iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADE
Enable forwarding
/etc/sysctl.conf
net.ipv4.ip_forward=1
Reload: sysctl -p
Generate keys
KEYDIR=/root/keys
rm -rf $KEYDIR/*
#C=Country code
#O=Organisation
#CN=Server FQDN
echo generating CA Certificate
ipsec pki --gen --outform pem > $KEYDIR/caKey.pem
ipsec pki --self --in $KEYDIR/caKey.pem --dn "C=NL, O=org, CN=vpn.org.nl" --ca --outform pem > $KEYDIR/caCert.pem
echo generating Server certificate
ipsec pki --gen --outform pem > $KEYDIR/serverKey.pem
ipsec pki --pub --in $KEYDIR/serverKey.pem | ipsec pki --issue --cacert $KEYDIR/caCert.pem --cakey $KEYDIR/caKey.pem \
--dn "C=NL, O=org, CN=vpn.org.nl" --san="vpn.org.nl" \
--flag serverAuth --flag ikeIntermediate --outform pem > $KEYDIR/serverCert.pem
echo generating Client certificate
ipsec pki --gen --outform pem > $KEYDIR/clientKey.pem
ipsec pki --pub --in $KEYDIR/clientKey.pem | ipsec pki --issue --cacert $KEYDIR/caCert.pem --cakey $KEYDIR/caKey.pem \
--dn "C=NL, O=org, CN=client" --outform pem > $KEYDIR/clientCert.pem
echo generating PKCS12 file
openssl pkcs12 -export -inkey $KEYDIR/clientKey.pem -in $KEYDIR/clientCert.pem -name "client" \
-certfile $KEYDIR/caCert.pem -caname "vpn.org.nl" -out $KEYDIR/clientCert.p12
echo Copy keys
cp $KEYDIR/caCert.pem /usr/local/etc/ipsec.d/cacerts/
cp $KEYDIR/serverCert.pem /usr/local/etc/ipsec.d/certs/
cp $KEYDIR/serverKey.pem /usr/local/etc/ipsec.d/private/
cp $KEYDIR/clientCert.pem /usr/local/etc/ipsec.d/certs/
cp $KEYDIR/clientKey.pem /usr/local/etc/ipsec.d/private/
Configure IPsec
/usr/local/etc/ipsec.conf
config setup
conn iososx
keyexchange=ikev1
authby=xauthrsasig
xauth=server
left=%defaultroute
leftsubnet=0.0.0.0/0
leftfirewall=yes
leftcert=serverCert.pem
right=%any
rightsubnet=10.0.0.0/24
rightsourceip=10.0.0.2
rightcert=clientCert.pem
auto=add
/usr/local/etc/ipsec.secrets
: RSA serverKey.pem yourusername : XAUTH "yourpassword"
/usr/local/etc/strongswan.conf
# for strongSwan 5.0.0+
charon {
dns1 = 1.2.3.4 #your DNS servers
dns2 = 2.3.4.5
}
Stop/start/status IPsec and logging
Status:
ipsec status
Stop:
ipsec stop
Start:
ipsec start
Logging: /var/log/syslog
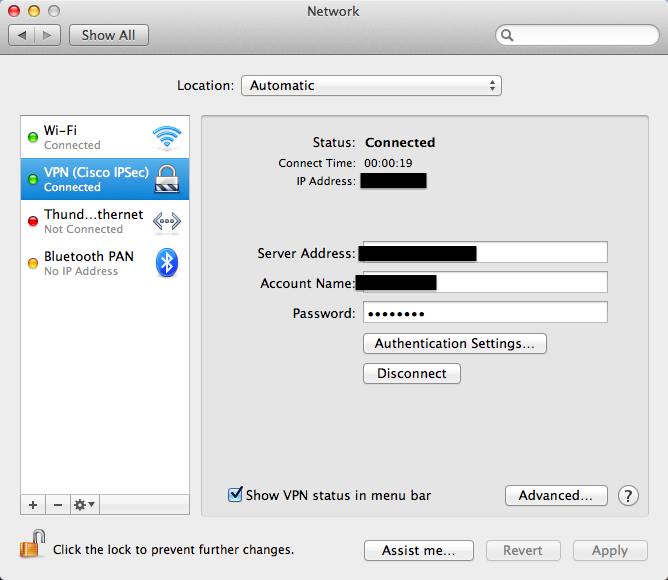
Configure OS X
For Mac OS X, open Keychain.app and import the clientCert.p12 into the System keychain, then mark as “Always Trusted”. If you're running into trouble with the negotiation, make sure that in the Access Control tab of the private key, all applications are allowed to access it.
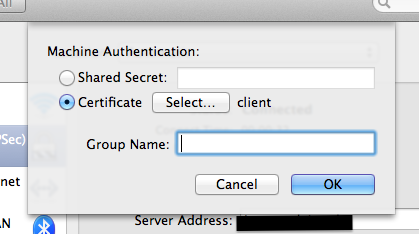
Configure VPN
Troubleshooting
Entropy
If 'ipsec pki' seems to hang, you probably don't have enough entropy. Install haveged.
apt-get install haveged
You can check the available entropy:
cat /proc/sys/kernel/random/entropy_avail
Test your IP-address
strongswan_ipsec_os_x.txt · Last modified: 2021/10/09 15:14 by 127.0.0.1